Unphishable authentication doesn't exist; but it is possible to make deception more difficult. I'm going to present an approach that eliminates some potential attacks.
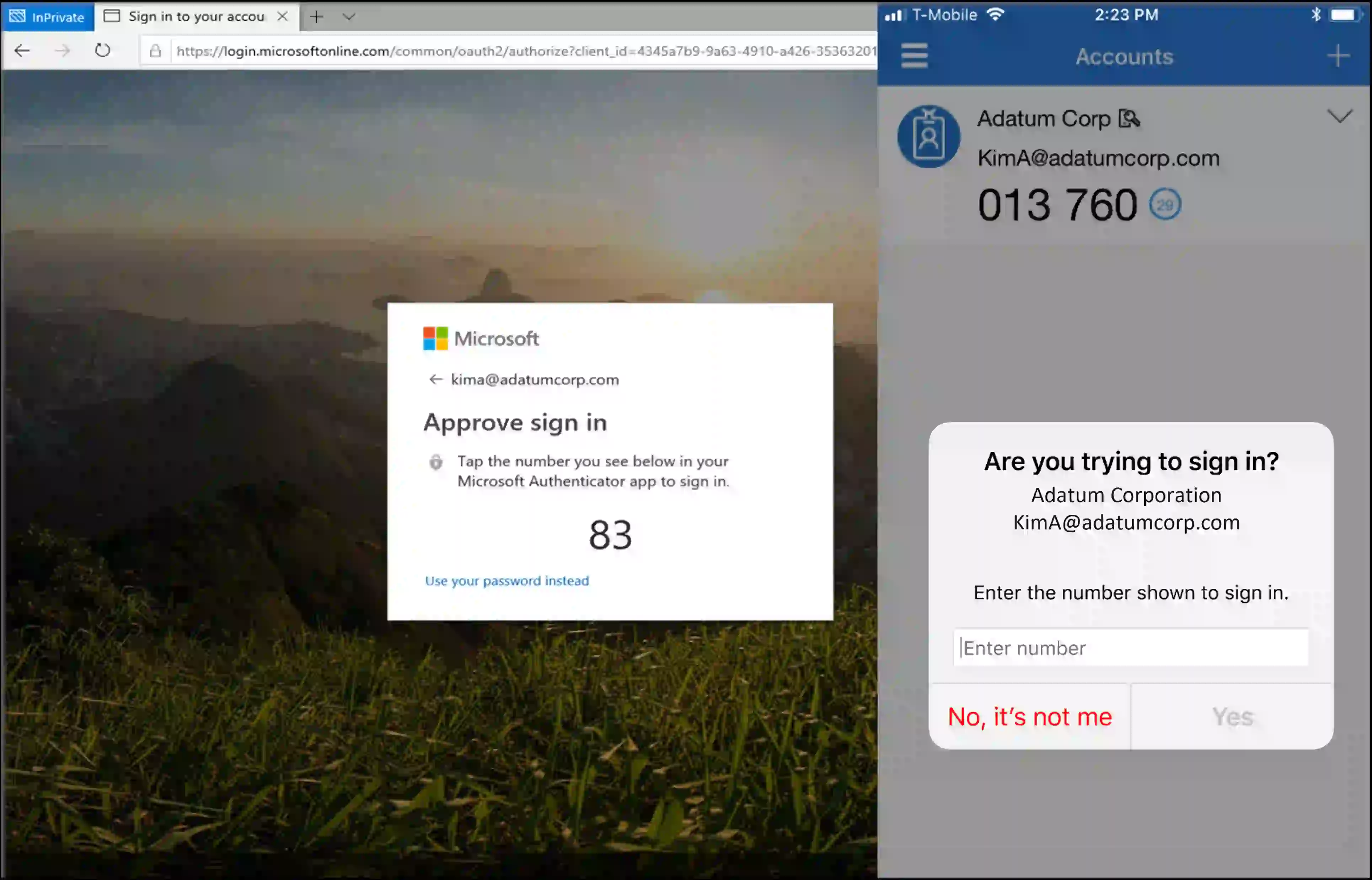
Let's look at an example of number matching 2FA:
While more secure than ordinary push 2fa, users that don't read the
hostname could still be phished. Domain matching 2FA solves this problem
by replacing the number with a domain.
Let's take a look at this in action.
Here are a couple of notes:
- Domains should vary: using 1 domain may cause users to simply remember and re-enter that domain (it is possible to implement a similar approach with 1 domain; I'll expand on this later).
- For maximum security, a large pool of domains with varying TLDs would be necessary. This would require the user to fully read the domain.
- Phishing is still possible (note the red warning text on the demo); an attacker could convince a victim to go against instructions and enter a non-matching domain.
- That really cool browser in browser phish would probably still work
- Being annoying and persistent is still possible, although the attacker would have to contact the victim which might tip them off that something is happening
- Users may start to think that sketchy URLs are legitimate and fall for other phishing attacks